Usually, Safe Boot prevents the UEFI from working all subsequent information except they bear a digital signature certifying these information are trusted by the system maker. The exploit bypasses this safety by injecting shell code stashed in a malicious bitmap picture displayed by the UEFI in the course of the boot-up course of. The injected code installs a cryptographic key that digitally indicators a malicious GRUB file together with a backdoored picture of the Linux kernel, each of which run throughout later phases of the boot course of on Linux machines.
The silent set up of this key induces the UEFI to deal with the malicious GRUB and kernel picture as trusted elements, and thereby bypass Safe Boot protections. The ultimate result’s a backdoor slipped into the Linux kernel earlier than some other safety defenses are loaded.
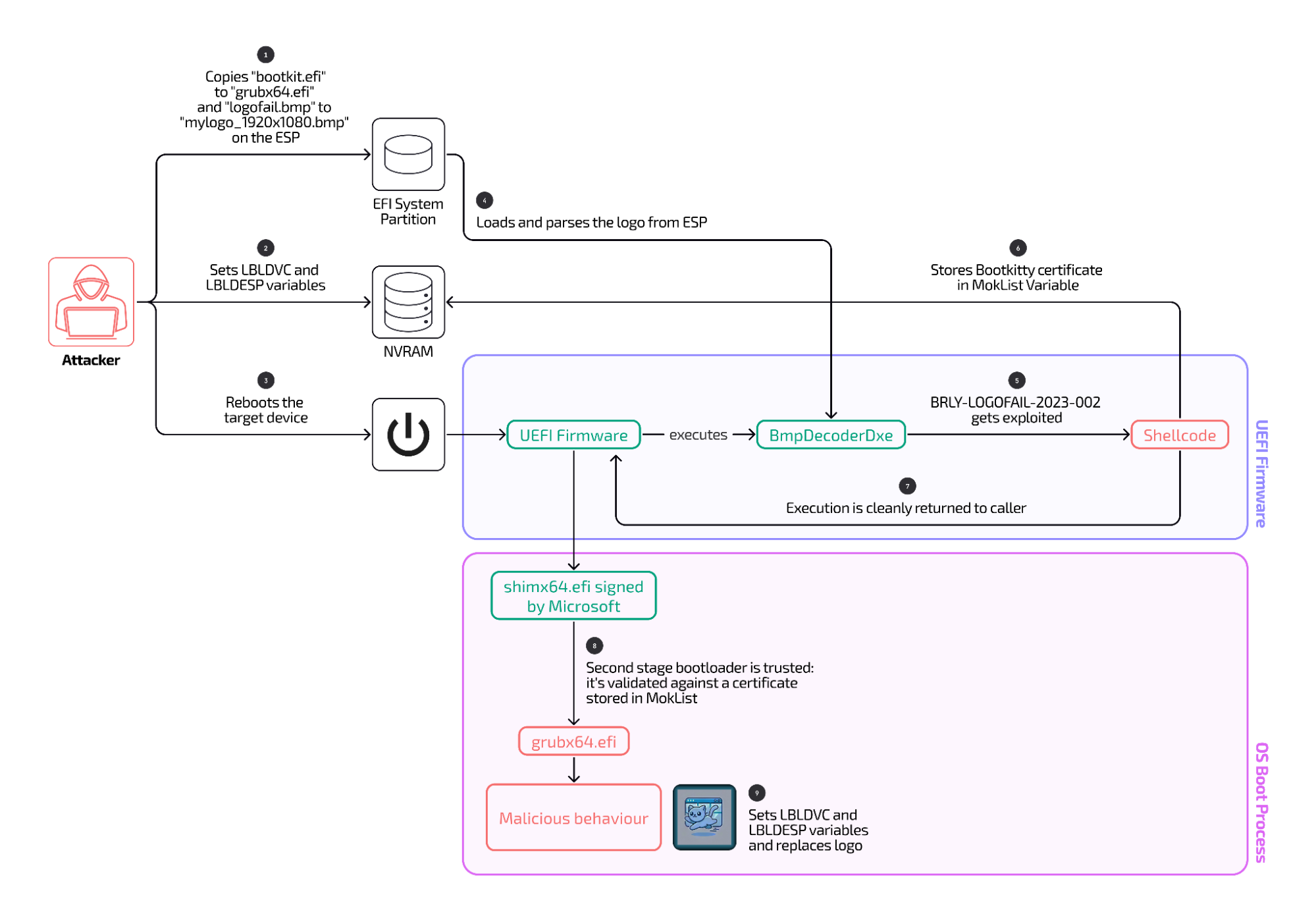
Diagram illustrating the execution movement of the LogoFAIL exploit Binarly discovered within the wild.
Credit score:
Binarly
In a web based interview, HD Moore, CTO and co-founder at runZero and an professional in firmware-based malware, defined the Binarly report this fashion:
The Binarly paper factors to somebody utilizing the LogoFAIL bug to configure a UEFI payload that bypasses safe boot (firmware) by tricking the firmware into accepting their self-signed key (which is then saved within the firmware because the MOK variable). The evil code continues to be restricted to the user-side of UEFI, however the LogoFAIL exploit does allow them to add their very own signing key to the firmware’s enable listing (however doesn’t infect the firmware in any approach in any other case).
It is nonetheless successfully a GRUB-based kernel backdoor versus a firmware backdoor, nevertheless it does abuse a firmware bug (LogoFAIL) to permit set up with out person interplay (enrolling, rebooting, then accepting the brand new MOK signing key).
In a traditional safe boot setup, the admin generates a neighborhood key, makes use of this to signal their up to date kernel/GRUB packages, tells the firmware to enroll the important thing they made, then after reboot, the admin has to simply accept this new key by way of the console (or remotely by way of bmc/ipmi/ilo/drac/and so on bios console).
On this setup, the attacker can substitute the known-good GRUB + kernel with a backdoored model by enrolling their very own signing key with out person interplay by way of the LogoFAIL exploit, nevertheless it’s nonetheless successfully a GRUB-based bootkit, and would not get hardcoded into the BIOS firmware or something.
Machines weak to the exploit embody some fashions bought by Acer, HP, Fujitsu, and Lenovo after they ship with a UEFI developed by producer Insyde and run Linux. Proof discovered within the exploit code signifies the exploit could also be tailor-made for particular {hardware} configurations of such machines. Insyde issued a patch earlier this yr that stops the exploit from working. Unpatched units stay weak. Units from these producers that use non-Insyde UEFIs aren’t affected.
Usually, Safe Boot prevents the UEFI from working all subsequent information except they bear a digital signature certifying these information are trusted by the system maker. The exploit bypasses this safety by injecting shell code stashed in a malicious bitmap picture displayed by the UEFI in the course of the boot-up course of. The injected code installs a cryptographic key that digitally indicators a malicious GRUB file together with a backdoored picture of the Linux kernel, each of which run throughout later phases of the boot course of on Linux machines.
The silent set up of this key induces the UEFI to deal with the malicious GRUB and kernel picture as trusted elements, and thereby bypass Safe Boot protections. The ultimate result’s a backdoor slipped into the Linux kernel earlier than some other safety defenses are loaded.

Diagram illustrating the execution movement of the LogoFAIL exploit Binarly discovered within the wild.
Credit score:
Binarly
In a web based interview, HD Moore, CTO and co-founder at runZero and an professional in firmware-based malware, defined the Binarly report this fashion:
The Binarly paper factors to somebody utilizing the LogoFAIL bug to configure a UEFI payload that bypasses safe boot (firmware) by tricking the firmware into accepting their self-signed key (which is then saved within the firmware because the MOK variable). The evil code continues to be restricted to the user-side of UEFI, however the LogoFAIL exploit does allow them to add their very own signing key to the firmware’s enable listing (however doesn’t infect the firmware in any approach in any other case).
It is nonetheless successfully a GRUB-based kernel backdoor versus a firmware backdoor, nevertheless it does abuse a firmware bug (LogoFAIL) to permit set up with out person interplay (enrolling, rebooting, then accepting the brand new MOK signing key).
In a traditional safe boot setup, the admin generates a neighborhood key, makes use of this to signal their up to date kernel/GRUB packages, tells the firmware to enroll the important thing they made, then after reboot, the admin has to simply accept this new key by way of the console (or remotely by way of bmc/ipmi/ilo/drac/and so on bios console).
On this setup, the attacker can substitute the known-good GRUB + kernel with a backdoored model by enrolling their very own signing key with out person interplay by way of the LogoFAIL exploit, nevertheless it’s nonetheless successfully a GRUB-based bootkit, and would not get hardcoded into the BIOS firmware or something.
Machines weak to the exploit embody some fashions bought by Acer, HP, Fujitsu, and Lenovo after they ship with a UEFI developed by producer Insyde and run Linux. Proof discovered within the exploit code signifies the exploit could also be tailor-made for particular {hardware} configurations of such machines. Insyde issued a patch earlier this yr that stops the exploit from working. Unpatched units stay weak. Units from these producers that use non-Insyde UEFIs aren’t affected.


















