Because the video explains:
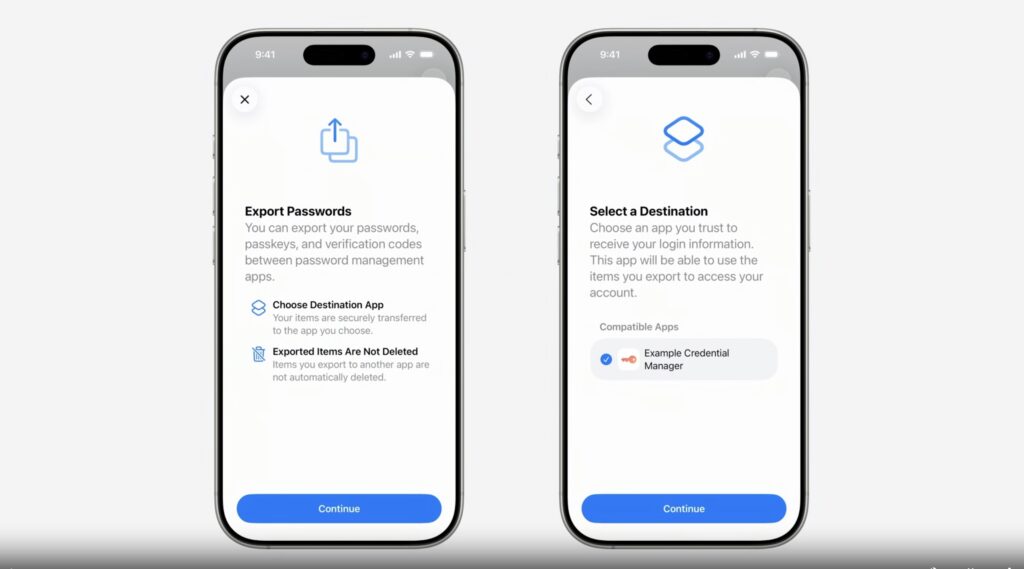
This new course of is essentially totally different and safer than conventional credential export strategies, which frequently contain exporting an unencrypted CSV or JSON file, then manually importing it into one other app. The switch course of is consumer initiated, happens instantly between taking part credential supervisor apps and is secured by native authentication like Face ID.
This switch makes use of an information schema that was in-built collaboration with the members of the FIDO Alliance. It standardizes the info format for passkeys, passwords, verification codes, and extra information sorts.
The system gives a safe mechanism to maneuver the info between apps. No insecure information are created on disk, eliminating the chance of credential leaks from exported information. It’s a contemporary, safe solution to transfer credentials.
The push to passkeys is fueled by the large prices related to passwords. Creating and managing a sufficiently lengthy, randomly generated password for every account is a burden on many customers, a problem that always results in weak selections and reused passwords. Leaked passwords have additionally been a persistent drawback.
Passkeys, in principle, present a way of authentication that’s resistant to credential phishing, password leaks, and password spraying. Below the most recent “FIDO2” specification, it creates a singular public/non-public encryption keypair throughout every web site or app enrollment. The keys are generated and saved on a consumer’s telephone, pc, YubiKey, or related system. The general public portion of the hot button is despatched to the account service. The non-public key stays sure to the consumer system, the place it may well’t be extracted. Throughout sign-in, the web site or app server sends the system that created the important thing pair a problem within the type of pseudo-random information. Authentication happens solely when the system indicators the problem utilizing the corresponding non-public key and sends it again.
This design ensures that there isn’t any shared secret that ever leaves the consumer’s system. Which means there is not any information to be sniffed in transit, phished, or compromised by way of different frequent strategies.
As I famous in December, the most important factor holding again passkeys for the time being is their lack of usability. Apps, OSes, and web sites are, in lots of instances, islands that do not interoperate with their friends. In addition to probably locking customers out of their accounts, the dearth of interoperability additionally makes passkeys too tough for many individuals.
Apple’s demo this week gives the strongest indication but that passkey builders are making significant progress in enhancing usability.

Because the video explains:
This new course of is essentially totally different and safer than conventional credential export strategies, which frequently contain exporting an unencrypted CSV or JSON file, then manually importing it into one other app. The switch course of is consumer initiated, happens instantly between taking part credential supervisor apps and is secured by native authentication like Face ID.
This switch makes use of an information schema that was in-built collaboration with the members of the FIDO Alliance. It standardizes the info format for passkeys, passwords, verification codes, and extra information sorts.
The system gives a safe mechanism to maneuver the info between apps. No insecure information are created on disk, eliminating the chance of credential leaks from exported information. It’s a contemporary, safe solution to transfer credentials.
The push to passkeys is fueled by the large prices related to passwords. Creating and managing a sufficiently lengthy, randomly generated password for every account is a burden on many customers, a problem that always results in weak selections and reused passwords. Leaked passwords have additionally been a persistent drawback.
Passkeys, in principle, present a way of authentication that’s resistant to credential phishing, password leaks, and password spraying. Below the most recent “FIDO2” specification, it creates a singular public/non-public encryption keypair throughout every web site or app enrollment. The keys are generated and saved on a consumer’s telephone, pc, YubiKey, or related system. The general public portion of the hot button is despatched to the account service. The non-public key stays sure to the consumer system, the place it may well’t be extracted. Throughout sign-in, the web site or app server sends the system that created the important thing pair a problem within the type of pseudo-random information. Authentication happens solely when the system indicators the problem utilizing the corresponding non-public key and sends it again.
This design ensures that there isn’t any shared secret that ever leaves the consumer’s system. Which means there is not any information to be sniffed in transit, phished, or compromised by way of different frequent strategies.
As I famous in December, the most important factor holding again passkeys for the time being is their lack of usability. Apps, OSes, and web sites are, in lots of instances, islands that do not interoperate with their friends. In addition to probably locking customers out of their accounts, the dearth of interoperability additionally makes passkeys too tough for many individuals.
Apple’s demo this week gives the strongest indication but that passkey builders are making significant progress in enhancing usability.



















