Creating or modifying good contracts usually price lower than $2 per transaction, an enormous financial savings by way of funds and labor over extra conventional strategies for delivering malware.
Layered on high of the EtherHiding Google noticed was a social-engineering marketing campaign that used recruiting for faux jobs to lure targets, lots of whom have been builders of cryptocurrency apps or different on-line companies. Through the screening course of, candidates should carry out a check demonstrating their coding or code-review expertise. The information required to finish the exams are embedded with malicious code.
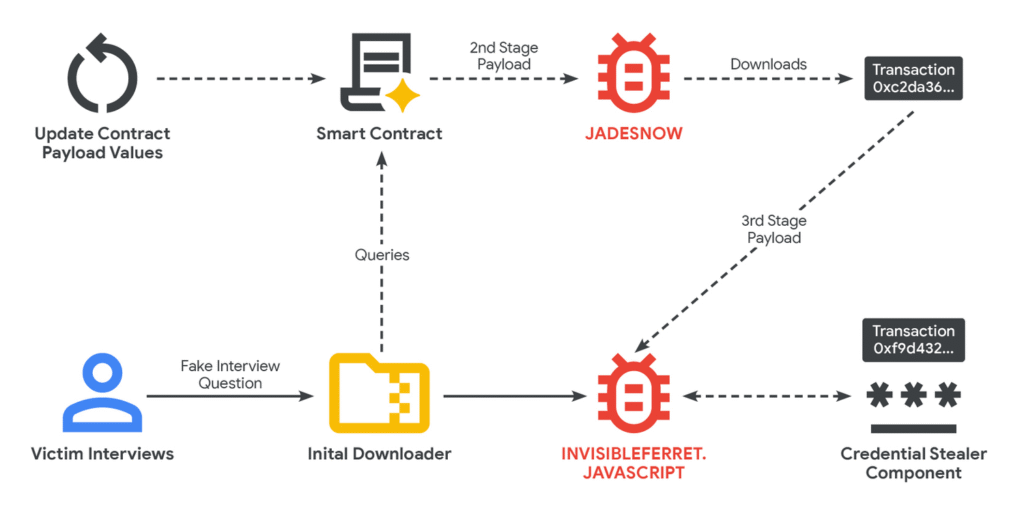
Illustration of UNC5342 EtherHiding circulation.
The an infection course of depends on a series of malware that will get put in in phases. Later phases accountable for executing the ultimate payloads are then put in via good contracts that the hackers retailer on the Ethereum and the BNB Sensible Chain blockchains, which settle for uploads from anybody.
One of many teams Google noticed, a North Korean-backed workforce tracked as UNC5342, makes use of earlier-stage malware tracked as JadeSnow to retrieve later-stage malware from each the BNB and Ethereum blockchains. The Google researchers noticed:
It’s uncommon to see a menace actor make use of a number of blockchains for EtherHiding exercise; this may increasingly point out operational compartmentalization between groups of North Korean cyber operators. Lastly, campaigns incessantly leverage EtherHiding’s versatile nature to replace the an infection chain and shift payload supply areas. In a single transaction, the JADESNOW downloader can change from fetching a payload on Ethereum to fetching it on the BNB Sensible Chain. This change not solely complicates evaluation but in addition leverages decrease transaction charges supplied by alternate networks.
The researchers mentioned in addition they noticed one other group, the financially motivated UNC5142, additionally using EtherHiding.
North Korea’s hacking prowess was as soon as thought-about low caliber. Over the previous decade, the nation has mounted a collection of high-profile assault campaigns that reveal rising ability, focus, and sources. Two weeks in the past, blockchain evaluation agency Elliptic mentioned the nation has stolen cryptocurrency valued at greater than $2 billion to date in 2025.
Creating or modifying good contracts usually price lower than $2 per transaction, an enormous financial savings by way of funds and labor over extra conventional strategies for delivering malware.
Layered on high of the EtherHiding Google noticed was a social-engineering marketing campaign that used recruiting for faux jobs to lure targets, lots of whom have been builders of cryptocurrency apps or different on-line companies. Through the screening course of, candidates should carry out a check demonstrating their coding or code-review expertise. The information required to finish the exams are embedded with malicious code.
Illustration of UNC5342 EtherHiding circulation.
The an infection course of depends on a series of malware that will get put in in phases. Later phases accountable for executing the ultimate payloads are then put in via good contracts that the hackers retailer on the Ethereum and the BNB Sensible Chain blockchains, which settle for uploads from anybody.
One of many teams Google noticed, a North Korean-backed workforce tracked as UNC5342, makes use of earlier-stage malware tracked as JadeSnow to retrieve later-stage malware from each the BNB and Ethereum blockchains. The Google researchers noticed:
It’s uncommon to see a menace actor make use of a number of blockchains for EtherHiding exercise; this may increasingly point out operational compartmentalization between groups of North Korean cyber operators. Lastly, campaigns incessantly leverage EtherHiding’s versatile nature to replace the an infection chain and shift payload supply areas. In a single transaction, the JADESNOW downloader can change from fetching a payload on Ethereum to fetching it on the BNB Sensible Chain. This change not solely complicates evaluation but in addition leverages decrease transaction charges supplied by alternate networks.
The researchers mentioned in addition they noticed one other group, the financially motivated UNC5142, additionally using EtherHiding.
North Korea’s hacking prowess was as soon as thought-about low caliber. Over the previous decade, the nation has mounted a collection of high-profile assault campaigns that reveal rising ability, focus, and sources. Two weeks in the past, blockchain evaluation agency Elliptic mentioned the nation has stolen cryptocurrency valued at greater than $2 billion to date in 2025.